Our IT service company specializes in cyber security and AI solutions for businesses worldwide. Our team of experts provides comprehensive training programs in cyber security, data management, UX design, and design thinking to help companies stay ahead of the curve.
Training
Through the TCST London Academy, we deliver quality training and certification programs, tailored for individuals and teams working in cybersecurity field.
Check our portfolio of training programs by visiting the academy or by exploring our training programs below :
- Cyber Security Introduction
- Ethical Offensive Cybersecurity
- Digital Forensics
- Cryptography
- Kali Linux
- Threat Intelligence
- IoT Security.
- International Cyber Conflicts.
SOC (Security Operation Center)
We provide end to end solutions to our customers in order to guaranty the perfect adaptation with legacy systems. We offer:
- End-point security project: Our experts can help businesses design and implement an end-point security solution that protects their devices from cyber attacks. We can work with businesses to identify the right security tools, train their employees on best practices, and monitor their devices for potential threats.
- Mobile device management (MDM): With the increasing use of mobile devices in the workplace, businesses need to have a comprehensive MDM solution in place. Our team can help businesses design and implement an MDM solution that ensures the security of their mobile devices and data.
- Network security: A strong network security solution is essential to protect businesses from cyber attacks. Our team can help businesses design and implement a network security solution that includes firewalls, intrusion detection and prevention, and VPNs.
- Security operations center (SOC) implementation: A SOC is a critical component of a business’s security infrastructure. Our team can help businesses design and implement a SOC that provides real-time monitoring and threat analysis.
Managed Security Service Provider (MSSP)
A managed security service provider (MSSP) is an information technology (IT) service provider that promotes security services to businesses. The role of an MSSP is to help protect businesses from security threats, whether that means providing software and services that keep company data safe or building a network of security experts who can respond to attacks as they happen.
MSSPs provide cybersecurity monitoring and management, which may include virus and spam blocking, intrusion detection, firewalls and virtual private network (VPN) management. MSSPs also handle matters such as system changes, modifications and upgrades.
AT TCSC Solutions we provide the six main categories of managed security services, including:
- On-site consulting
- Perimeter management of the client’s network
- Product resale
- Managed security monitoring
- Penetration testing and vulnerability assessments
- compliance monitoring.
Security Audit
Audit: Our team can perform a comprehensive security audit of a business’s systems to identify potential vulnerabilities and provide recommendations for improvement.
We can help our customers in fields such as:
- Standards and Frameworks Implementation and audit: ISO27001, PCI/DSS, KYC…
- Vulnerability analysis: Our experts can conduct a vulnerability analysis of a business’s systems to identify potential weaknesses and develop a plan to mitigate them.
- Risk assessment: Our team can perform a risk assessment to identify potential threats and assess their impact on a business’s operations.
- Security audit: A comprehensive security audit is essential to ensure that a business’s systems are secure. Our team can perform a security audit and provide recommendations for improvement.
Compliance
Our Company partnered recently with one of the most promising solution editors in the sector of Internal Threat Detection and Prevention “SearchInform”, this is not just a partnership, we believe in core values of our partner, hence we promote their solution over other well-known actors that provide the same range of products.

SearchInform products line includes 6 solutions that enable comprehensive control and predict insider risks at all levels of a company’s information system.
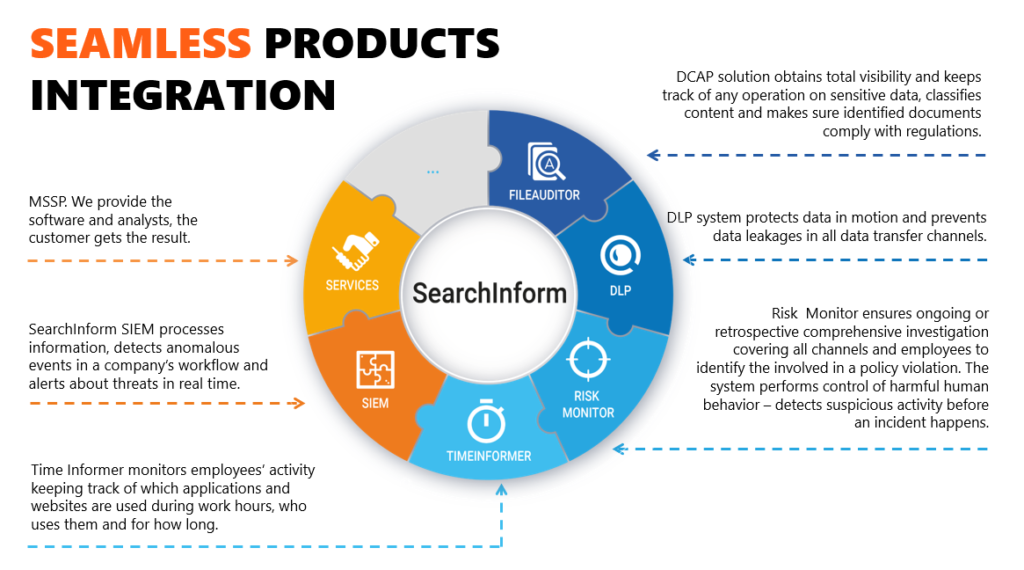
If you are interested by one product, please feel free to contact us. We will obtain a free demonstration and a POC
File & Data Protection
One of the best solutions we tested so far is our Partner’s solution SearchInform Risk Monitor for Internal Control and Fraud prevention:
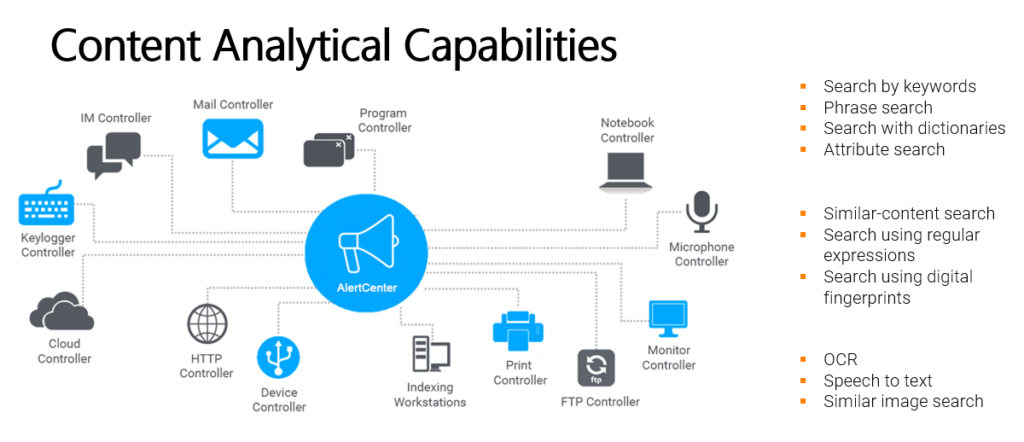
Contact one of our representatives for more details.
IoT Security solutions
IoT solutions and equipment architecture and dimensioning: We help businesses design and implement a security solution that includes the right tools and equipment, tailored to the specific needs of your operations. We provide: guidance on equipment architecture and dimensioning to ensure optimal performance and security for your IoT projects.
Integration of AI into Cyber Security solutions
In addition to our comprehensive cyber security and AI solutions, our company offers new technology consulting services to help businesses stay ahead of emerging trends. Our team of experts is experienced in a range of new technologies, including blockchain, quantum computing, and machine learning.
Threat Management and Threat Intelligence
- Threat management: Businesses need to have a comprehensive threat management solution in place to protect their systems from cyber attacks. Our team can help businesses identify potential threats, assess their impact, and develop a response plan.
- Threat intelligence: Threat intelligence is essential for businesses to stay ahead of emerging threats. Our team can help businesses collect and analyze threat intelligence data to identify potential threats and take proactive measures to mitigate them.
We work closely with businesses to understand their needs and help them integrate the latest technology into their operations. Whether it’s exploring new opportunities, identifying potential risks, or finding ways to optimize performance, our technology consulting services provide the guidance and support businesses need to succeed in today’s rapidly evolving landscape.

Our new technology consulting services cover a wide range of topics to help businesses stay ahead of the curve. Here are some examples of use cases for our services:
Our Partners:



